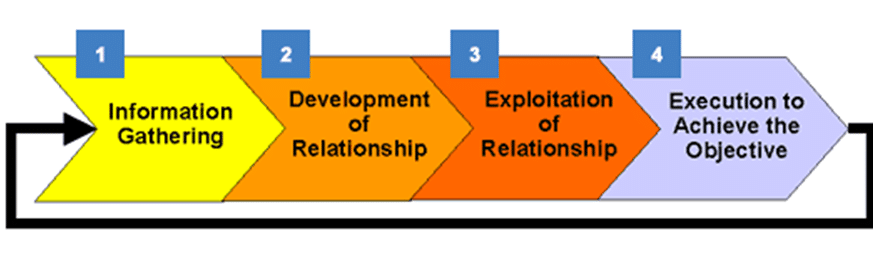
Social Engineering Risk Assessment
The human element is usually the weakest link in any security system. Even the tightest security systems can be defeated by a single person acting in an unauthorized manner. An attacker will frequently take advantage of an end user’s lack of knowledge about security awareness & security procedures. The purpose of this phase of a security risk assessment is to determine how successful a social engineering attack would be and the level of risk incurred by a social engineering attack.
Social engineers can also try to hit on the emotional part of people’s brains. They might try to take you on a guilt trip, make you nostalgic, or even try to impact negatively. The situation becomes alarming; people have the tendency to open up in front of the ones trying to give them emotional comfort. Some of the types social engineering attacks are phishing, pretexting, etc
Based on information gathered during other phases of the assessment and discussions with your firm, ShieldByte will craft and attempt for following social engineering attacks, customized to fit your company’s environment.